WordPress Hack Attempts
Running a website, both this one and others I am involved with, grants a different view on the ‘hacking’ that is often reported in the news. For one thing, attacks are more or less constant. An unfortunate part of having an internet accessible computer, someone is bound to poke at it. So I do what I can to defend against those attacks.
The root of my domain, dannybassette.com, is about as safe as it can be. Simple html, no scripts or anything of that nature. Doesn’t mean it’s immune to hacking, just means the portion of the site I have control over is not likely to be the weakest link.
My two sub-domains, at drat.dannybassette.com and ofal.dannybassette.com, are very different. As they are running code (WordPress), and not just handing back static html, there is actually something there to attack. And I see those attacks in the logs. Or would, if I bothered to sort through the nearly constant stream of them. I’ll glance at them from time to time, but it’s mostly not worth looking at.
User Does Not Exist
On the other hand, I do periodically look at the login attempts. To the best of my knowledge, none of the frequent attempts to get in have used a valid user name. Plenty of potential obvious ones, but so far, none of the actual accounts. But then again, that is something I did deliberately. The actual admin account does not have an obvious name.
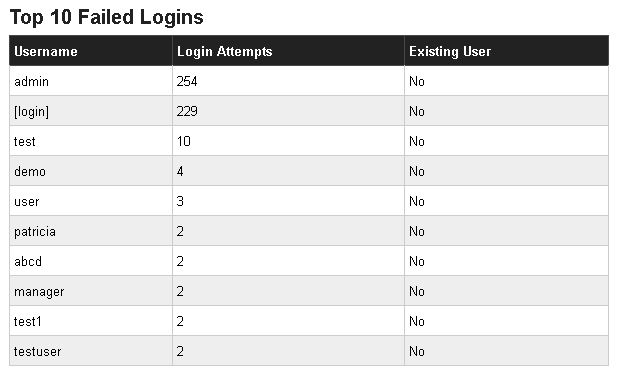
Due to the way WordPress works, posts (such as this one) do have to be linked to someone. So there is another account, that is NOT an admin. That one is assigned all posts. Obscurity is not security, but obscurity can serve as part of a defense strategy. If only because it points attackers away from what you want protected, so they waste their time elsewhere.
In the event attempts to log in to the ‘real’ account occur, well then I can make a new admin account. While it is not currently truly random, it could be. After all, the admin account doesn’t have to interact with ‘real’ people. Making both it and it’s password long random gibberish would only increase security. It’s not like I would have to remember it, into the password manager it would go.
When It Goes Wrong
At the end of the day, the attackers will win. They only have to get it right once, whereas the defender has to get it right every time. Until then, I do what I can for defense, as I keep my eyes open for their inevitable success.
Which is where backups come in to play. While a good backup doesn’t solve all problems, and isn’t the most efficient for others, it does solve many. And if nothing else, it means you always have the option of deleting the suspect content and restoring from a (presumably) known good backup.
At the risk of becoming a website about have this website…